Cisco powered first-ever hybrid G20 Summit in Indonesia
The Ministry of Communication and Information (Kominfo) of Indonesia tapped Cisco to power the first-ever hybrid G20 2022 Summit held in Bali, November 15-16.
Cisco...
Clough in Oz moves global ops to cloud with Oracle
Clough, a global engineering and construction company based in Australia, chose Oracle to modernise its back-office systems taking them from on-premises to the cloud.
Clough...
Heads rolled in 1 of 3 Singapore firms after cyberattack
IT and security leaders in Singapore must address, on average, one cyberattack per week according to results of a new study released by Rubrik...
Ransomware is not new, so why are businesses still falling for it?
Here are several things that businesses can do to improve their cyber hygiene and minimise the impact of ransomware.
Automation is not just RPA: Workato CIO
We spoke to Workato's Carter Busse about all things automation, including popular processes that customers use, and using automation in unexpected ways.
Why authenticity is the next big thing in managing threats
Using AI in an authentic manner is necessary in managing the risk of cyberthreats. Here are a few things that leaders should consider.
A distrustful digital supply chain is one that stays safe
Having a digital supply chain is a boon for businesses, but it comes with cybersecurity risks. Here are a few ways to mitigate them.
Dedicare grows medical practice in Hong Kong with cloud accounting
FastLane, a tech savvy accountant and advisor, has partnered with Xero to accelerate digital transformation by providing customised cloud accounting and business solutions for Dedicare in Hong...
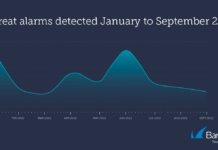
Vacation season leaves APAC firms vulnerable to cyberattack
Businesses in Asia-Pacific could find themselves vulnerable to attack during the vacation months, according to Barracuda, which analysed the latest threat insight from its...
Firms fret over lack of skilled staff as threats grow through cloud, IoT
Public key infrastructure (PKI) remains the cornerstone of nearly every IT security environment, but even as the technology matures, new use cases, and rising compliance...