The fragmented ecosystem of cyber defense controls is putting businesses at risk of exposure to increasingly troubling data breaches, according to Imperva.
With this warning, the cybersecurity firm said companies must improve visibility and monitoring of data access, eliminate logging and monitoring gaps in their cyber security strategy, and step up user education to keep their data safe.
Imperva said cybersecurity breaches are mounting as organisations hasten their digitisation efforts.
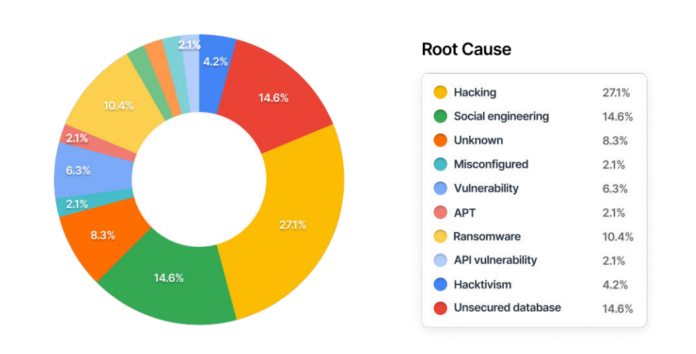
In 2022, the Imperva threat threat research team analysed over 100 of the largest and most well-known data breaches. The study revealed that a greater number and higher frequency of breaches has occurred in the last decade.
An increasing amount of stolen data is being exposed and sold on the dark web. Often, this is used in extortion attempts, to commit financial fraud, and as fuel to create phishing and other social engineering campaigns, which in turn leads to more data breaches.
Data breaches are caused by a variety of issues – such as poor security practices like using unprotected publicly accessible services (Microsoft, Advanced Info Service) or weak authentication.
Some victims also suffer a large fallout from a seemingly small error, such as forgetting about data left behind in temp files from ETL jobs and storing database passwords in clear text.
As enterprises turn to the cloud or work with partners already on the cloud, they are finding that the new IT environment requires a different and often more sophisticated set of controls to adequately secure.
Microservices, open-source code, and API are used when developing modern applications. Combined, these add to the cyber security challenge by organically widening an organisation’s risk footprint, often doing so without their awareness.
The common practice of using disparate cybersecurity tools also leave gaps in an organisation’s ability to identify and mitigate threats.
In interactions with customers in the region, Imperva has identified specific vulnerabilities that often go unattended or are inadvertently introduced — unauthenticated APIs; poorly secured application login points; broken application/API data authorisation; weakly designed and coded APIs; and poor practices around database integration and migration activities.
“These issues are hard to mitigate because most SOC teams do not have access to data-centric logging telemetry that tells them what is happening on a granular level, from the application/API layer all the way down to the database access level,” said Reinhart Hansen, director of technology at Imperva.
“Organisations are flying blind when it comes to identifying anomalous and abusive data access that could be a data breach in flight or a key indicator that a breach is about to happen,” said Hansen.
Imperva said that to overcome today’s complex cybersecurity challenges, enterprises have to focus on the lifecycle of the data for which they are responsible.
Specifically, firms should gain complete, automatic visibility into all data stores; know their “normal” data state; avoid overwhelming the SOC; implement plain language, actionable insights, and alerts; go beyond the platform; and train their people.
“In most of the breaches analysed by Imperva, the lack of in-depth security stands out as the main reason,” said Hansen.
“Actions organisations can take to tangibly improve their security posture include reducing the attack surface through better database security, separating their database and application servers, and diluting excessive privileges from key users,” he added.