The cyberthreat landscape has reached a new level of commercialisation and convenience for would-be attackers, with nearly all barriers to entry for committing cybercrime removed through the expansion of cybercrime-as-a-service, according to Sophos.
The cybersecurity firm’s 2023 Threat Report shows that criminal underground marketplaces like Genesis have long made it possible to buy malware and malware deployment services (“malware-as-a-service”), as well as to sell stolen credentials and other data in bulk.
Over the last decade, with the increasing popularity of ransomware, an entire “ransomware-as-a-service” economy sprung up. Now, in 2022, this “as-a-service” model has expanded, and nearly every aspect of the cybercrime toolkit—from initial infection to ways to avoid detection—is available for purchase.
Sean Gallagher, Sophos principal threat researcher, higher rung cybercriminals are now selling tools and capabilities that once were solely in the hands of some of the most sophisticated attackers as services to other actors.
“For example, this past year, we saw advertisements for OPSEC-as-a-service where the sellers offered to help attackers hide Cobalt Strike infections, and we saw scanning-a-service, which gives buyers access to legitimate commercial tools like Metasploit, so that they can find and then exploit vulnerabilities,” said Gallagher.
He added that the commoditisation of nearly every component of cybercrime is impacting the threat landscape and opening up opportunities for any type of attacker with any type of skill level.
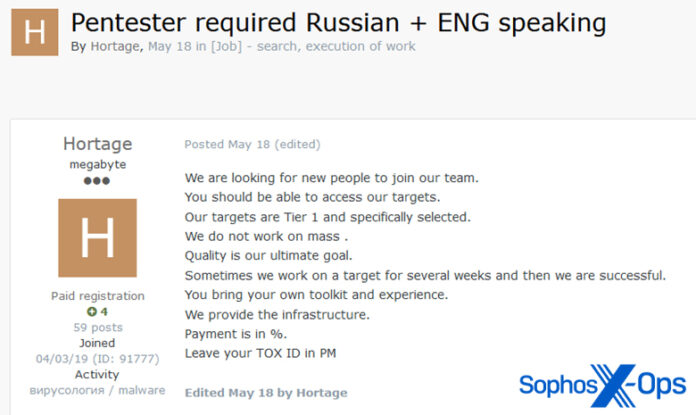
With the expansion of the “as-a-service” economy, underground cybercriminal marketplaces are also becoming increasingly commodified and are operating like mainstream businesses.
Cybercrime sellers are not just advertising their services but are also listing job offers to recruit attackers with distinct skills. Some marketplaces now have dedicated help-wanted pages and recruiting staff, while job seekers are posting summaries of their skills and qualifications.
“When we talk about the growing sophistication of the criminal underground, this extends to the world of ransomware,” said Gallagher.
For example, Lockbit 3.0 is now offering bug bounty programs for its malware and “crowd-sourcing” ideas to improve its operations from the criminal community. Other groups have moved to a “subscription model” for access to their leak data and others are auctioning it off.
Ransomware has become, first and foremost, a business. The evolving economics of the underground has not only incentivised the growth of ransomware and the “as-a-service” industry, but also increased the demand for credential theft.
With the expansion of web services, various types of credentials, especially cookies, can be used in numerous ways to gain a deeper foothold in networks, even bypassing MFA. Credential theft also remains one of the easiest ways for novice criminals to gain access to underground marketplaces and begin their “career.”